New blackmail technique through ransomware
During recent times the number of companies affected by Ransomware attacks has skyrocketed, which basically act in two ways: encrypting all the documents they find on the victim's network to ask for money in return of the decryption key, and/or by stealing a large amount of data to ask for money in exchange for not publishing it.
In general, the threat of local data encryption "usually", in quotes, is of less concern when companies have powerful backup systems, capable of reverting large amounts of data to its previous state in a short time time.
By the way, a detail that you should never forget when you are the victim of an attack of this type is, before trying to recover the data from the backup copies, make a new backup of the data as is, i.e. "encrypted". In this way, if for any reason full recovery proves impossible and unfortunately we had to access blackmail in some way, recovery would be possible. Otherwise, having crushed the encrypted data with the backup restore, we would have blocked this emergency exit without remedy.
However, more and more companies are affected by the second type of Ransomware, the one that exfiltrates data and threatens to publish it if we do not agree to a payment. The main reason is undoubtedly the RGPD (General Data Protection Regulation), since cyber-criminals know very well that companies may be more afraid of possible sanctions than of the damage caused by the publication of such data.
Usually, when a company is 'hacked' and data is extracted, those responsible for this company receive warning emails from cyber-criminals telling them what has happened, the steps to follow and to what is exposed in case of not doing it. The economic amounts vary, always in cryptocurrencies, between a few thousand Euros to several hundred million, increasing in value as more time passes.
Technicians from the Iberlayer Laboratory have detected today a new form of "blackmail", simple but very possibly effective: The cybercriminals, after stealing the data, have not only sent the threat to the victim as usual , instead they have sent emails to all the people and companies they have found in that stolen data, explaining what has happened and that if the victim does not agree to the blackmail, sorry, to the payment, it will be their data that will be made public.
Here is a real example of one of these emails:
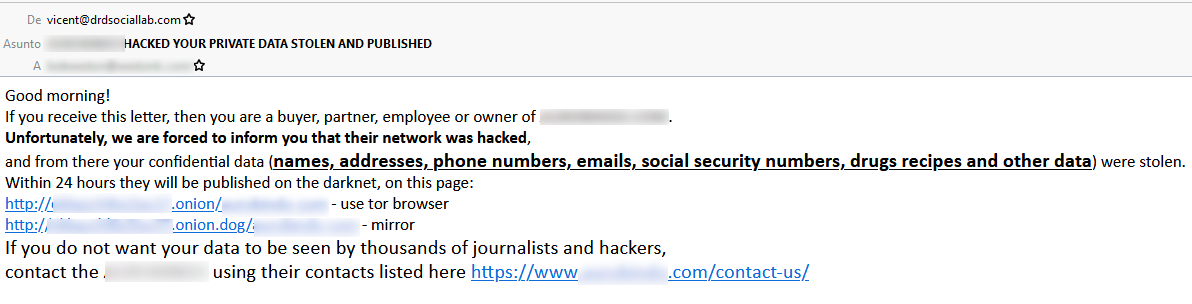
Obviously the objective is to exponentially multiply the pressure on the victim and end up paying.
It is a very simple idea and one that we fear is sadly going to work as expected, not only because of the pressure that a lot of third parties can exert, which of course, but because of the image that they have before them could have caused that company.
Our complete email protection solution, Iberlayer Email Guardian, provides the peace of mind that large companies need today regarding their email, detecting not only threats direct but also indirect, as safely as filtering by hand.
Pedro David Marco.
Iberlayer.com

